Sync .env files
sync .env files between machines, environments, and team members–from the creator of dotenv ★ 19.9k
Self-funded and profitable ⋅ Trusted by tens of thousands of companies worldwide
Works with a single command
You don't need to install anything to use dotenv-vault. No error prone binaries to install, infra to maintain, or custom code to write. It just works – with a single command.

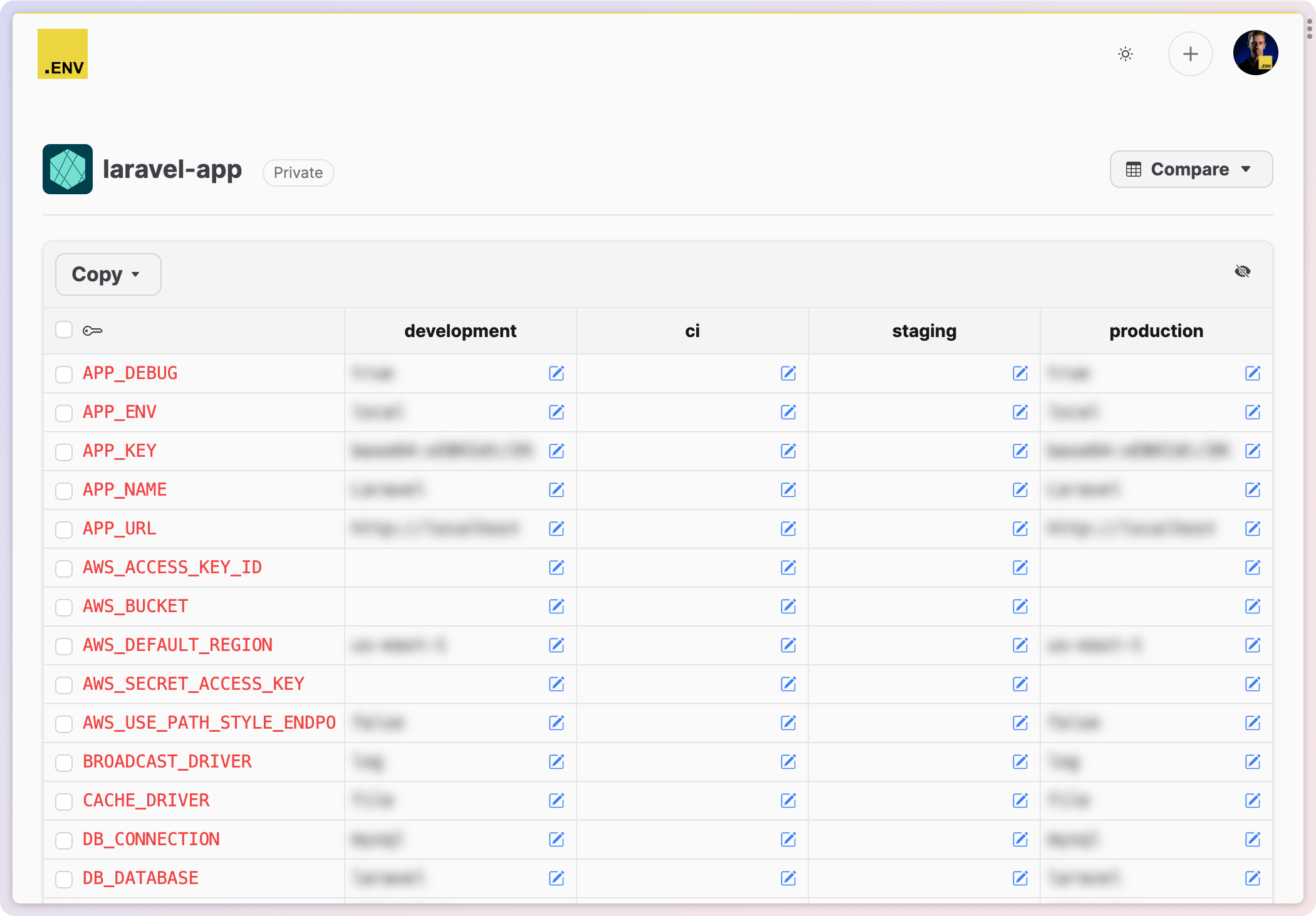
Multiple Environments
After you've pushed your .env file, you can manage your secrets across multiple environments. Open an environment to view and edit its environment variables.

Integrates Everywhere
Integrates everywhere you already write, test, build, and deploy your code. Generate your encrypted .env.vault file, commit that safely to code, and deploy. There's nothing else like it.


Teams love it
Each month, hundreds more software teams start using dotenv-vault.
From the same people that pioneered dotenv. Trusted by millions of developers worldwide.
Frequently asked questions
-
dotenv-vault is the only secrets manager that works with .env files instead of against them.
-
Other secrets managers make you replace your environment variables with remote API calls. This means you must rewrite your code, lock yourself into proprietary software, and possibly introduce new attack vectors to your software (It's generally easier for attackers to intercept your web traffic than to gain access to your file system.)
-
Your secrets go through a ten-step process to split their parts, encrypt those parts, and tokenize them into your project's vault. This includes using AES-GCM encryption - trusted by governments to transport top secret information. Read more about the ten-step process on the security page.
-
The .env.vault file is an encrypted version of your .env file. It is paired with a decryption key called the DOTENV_KEY. The DOTENV_KEY is set on your server or cloud hosting provider and the .env.vault file is committed to code.
-
Yes. AES-256 GCM encryption was developed for the needs of US Government agencies like the CIA. AES-256 takes billions of years to crack using current computing technology. Your secrets are much more likely to be leaked by a third-party. This is why we are so committed to this technology while everyone else is focused on syncing secrets to third-party integrations. We see a better way.
-
In the CircleCI breach the attacker accessed environment variables only. They could not access codebases. To steal your .env.vault secrets, an attacker needs need both – the decryption key (stored as an environment variable), AND the encrypted .env.vault file.
-
Not officially, but our goal is towards that. We're building things in a way that a cloud service is not necessary. As long as you can generate a .env.vault file you can use the technology. It is open to all.
-
The .env.vault file and its encryption algorithm is language-agnostic so technically it works with any language. We've built convenience libraries for it in a handful of languages and are adding more as requested. See the docs for a complete list.
-
See the install page. You can use npx, brew, and more.
Can’t find the answer you’re looking for? Send us an email at [email protected] team. We'd love to hear from you.











